WHAT TO EXPECT AT THE PIANO WORKS
Join us for dinner, drinks or brunch while our world class house musicians play your song requests.

Absolut Faithful
Ready to play?
Six shots. One imposter. No second chances.
Five shots will let you walk away smiling.
One will turn you into the imposter.
Will you reveal yourself - or pretend you're the same as everyone else?
How it works?
You will get a shot paddle of 6 Absolut Vodka flavoured shots.
One shot is secretly marked as the imposter shot.
The imposter one tastes... different.
BOOK NOWWHAT'S ON
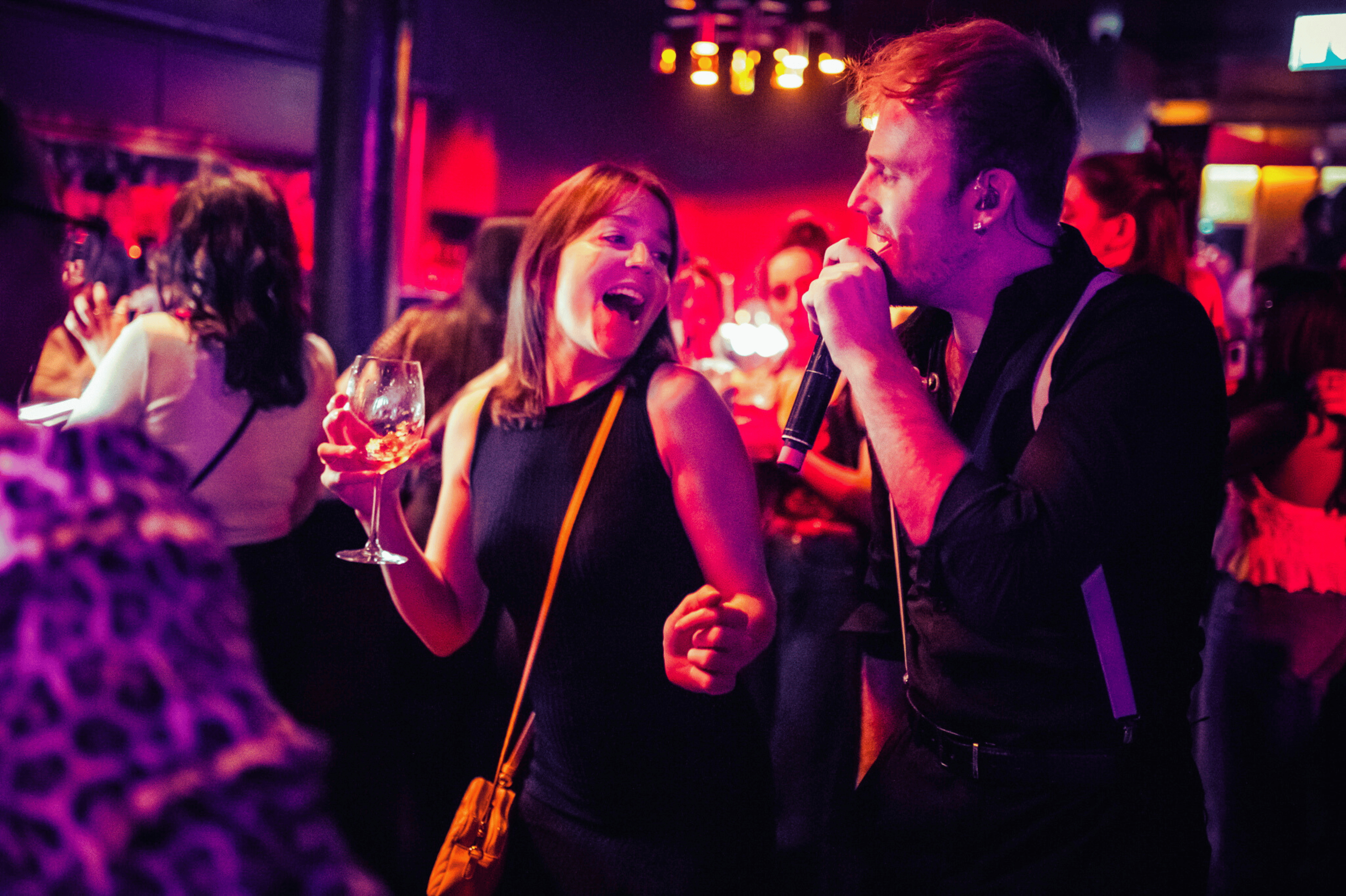
THE PIANO WORKS BRUNCH
90 minutes of bottomless drinks, two-course dining and non-stop live music
BOOK NOW

JAN 2026 HAPPY HOUR
At The Piano Works, January hits different. Between 1st January to the 29th January we’re counting you in with 5, 6, 7, 8 - our time-based cocktail offer designed to kickstart your night before the live music takes over. Click for more details...
JAN 2026 HAPPY HOUR

DINING
Delicious food, live music and an atmosphere like no other





